Zero Trust Architecture (ZTA) is a security model that eliminates complete trust and seeks to authenticate, authorise and continuously validate every entity, this includes entities attempting to gain access into an organization’s network as well as entities within the network. ZTA was introduced as an improvement on traditional security models which is based on a castle-and-moat concept. Using the castle-and-moat concept meant that focus was placed only on making it difficult to obtain access to a network.
WHY ZERO TRUST?
The problem with the castle-and-moat concept was that once an attacker is able to gain access to an organization’s network, they are free to move laterally which would lead to unauthorized access to resources and potential data exfiltration. This also holds true for malicious insiders as there is a lack of refined security controls within the network. With Zero Trust Architecture, every entity attempting to access a resource will be
continuously verified. The core principle behind it is to “never trust, and always verify” every entity.
THE DIFFERENT PRINCIPLES AND TECHNOLOGIES WITHIN ZERO TRUST ARCHITECTURE
Zero trust by design incorporates different principles and technologies like Identity and Access Management (IAM), Micro-segmentation, Least Privilege, and Data Loss Prevention (DLP) to name a few.
• Identity and Access Management: Zero Trust Architecture is achieved by using identities to create access policies. What this implies is that resource access within the network of an organization will be primarily based on the access privileges bestowed on each entity.
• Microsegmentation: Microsegmentation divides a network into small chucks which are accessed separately. In this setup each small chunk has its own set of security policies. This segmentation increases the security within the network of an organization because it will confine threats of breaches to a compromised segment without impact to the rest of the network.
• Least Privilege: This principle confers on an entity the minimum access required for its activities. With least privilege each entity is less exposed to sensitive parts of a network.
• Data Loss Prevention (DLP): Data Loss Prevention technology monitors and controls access to sensitive data within an organization. DLP will prevent data exfiltration in the event of a data breach.
IMPLEMENTING ZERO TRUST ARCHITECTURE
When implemented correctly, ZTA will lead to improved overall security while also reducing complexity.
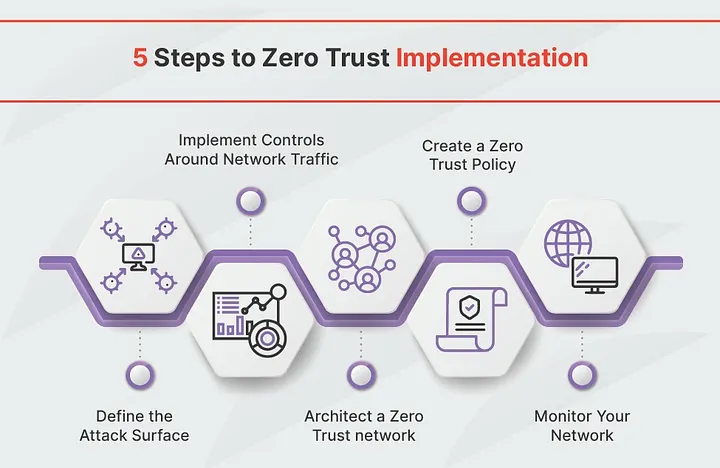
- Step 1: Define the attack surface and Identify critical Assets
This involves identifying sensitive assets and defining the potential attack surface withing the organization. By placing focus on the sensitive data, critical applications, and physical assets, an organization can simplify their approach to ZTA implementation and avoid getting overwhelmed with the deployment of security solutions across the network.
- Step 2: Implement Network Traffic Controls
To achieve this, every organization must understand how network traffic flows within its infrastructure, organizations must also understand the dependencies of each system. By conducting this analysis, organizations can make better decisions on what controls to use and how best to position them.
- Architect a Zero Trust Network
At this stage the Zero Trust Network must be tailored to the organisation’s needs and infrastructure. This would entail using some of the technologies spoken about earlier on like, Identity and Access Management (IAM), Microsegmentation, and Data Loss Prevention (DLP). Additional technologies include Multi-Factor Authentication, Unified Endpoint Management, and Security Information and Event Management (SIEM).
- Create a Zero Trust Policy
Organizations must create granular policies and controls that align with the principles of Zero Trust. Some of the important questions that should be considered when making this decision include who, what, when, where, why, and how for every entity that requires any form of access.
- Monitor the network
To fully realise the value of Zero Trust Architecture, an organization should monitor its network after implementation. This would provide visibility on what events are occurring and provide further insights on how to fine-tune policies.
BENEFITS / CONCLUSION
From a wholistic viewpoint, implementing Zero Trust Architecture however restricting it may seem has no downside to it. It will provide a considerably more secure environment to defend against unauthorised access to sensitive data and digital assets. ZTA will also help to improve the accuracy of the inventory of assets within an organization which could easily be translated to visibility. As you may know a lack of visibility is one of the reasons many organizations get breached in the world today. To conclude this, implementing Zero Trust within every organization is very critical to its security posture given the widespread adoption of remote and hybrid work models across organizations. This security model will primarily reduce the attack surface of an organization which will in turn reduce the damage done and minimise the cost of recovery in the event of a breach.

